Exploring the Landscape of Cybersecurity Risks
As our reliance on technology increases, so does the complexity of cybersecurity risks. These threats can affect individuals, businesses, and governments alike, leading to significant consequences such as data breaches, financial losses, and reputational damage. In this blog, we’ll explore the diverse landscape of cybersecurity risks and how to navigate them effectively.
If you want to excel in this career path, then it is recommended that you upgrade your skills and knowledge regularly with the latest Cyber Security Online Training.

Understanding Cybersecurity Risks
Cybersecurity risks refer to potential threats that can compromise the confidentiality, integrity, or availability of digital information. These risks can arise from various sources, including cybercriminals, insider threats, and even natural disasters. Understanding these risks is essential for developing effective security strategies.
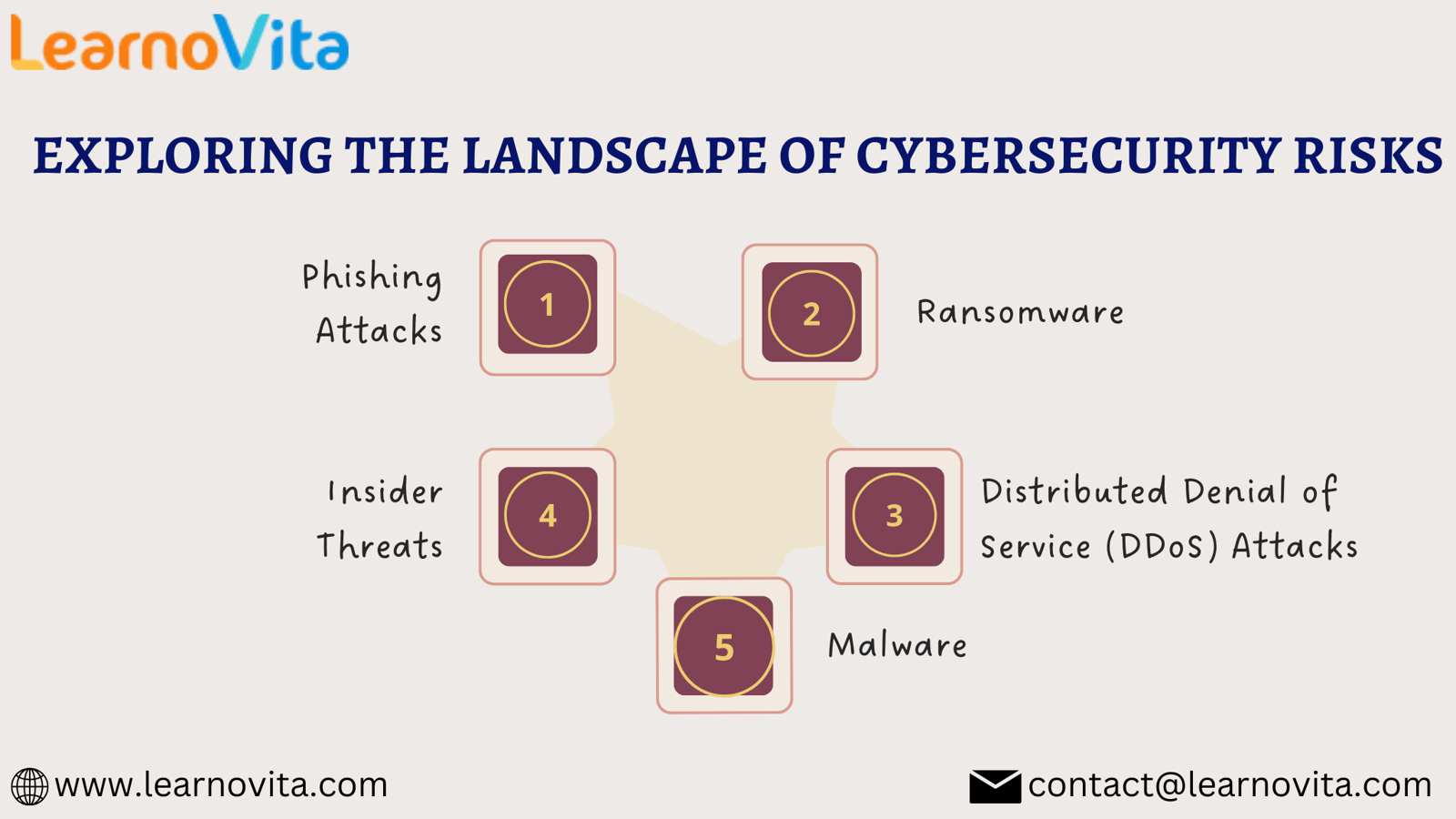
Key Types of Cybersecurity Risks
1. Phishing Attacks
Phishing attacks are among the most common cybersecurity risks. Cybercriminals use deceptive emails and messages that appear legitimate to trick individuals into revealing sensitive information. These attacks can lead to identity theft and financial loss. To mitigate this risk, always verify the sender’s identity and be cautious when clicking on links or downloading attachments.
2. Ransomware
Ransomware has emerged as a severe cybersecurity risk in recent years. This type of malware encrypts a victim's files, making them inaccessible until a ransom is paid. Organizations can suffer extensive operational disruptions and financial losses due to ransomware attacks. Regular data backups, employee training, and robust security measures are crucial for protection.
3. Malware
Malware encompasses a wide range of malicious software designed to harm or exploit systems. Types of malware include viruses, trojans, and spyware, each with its own methods of infiltration. Malware can spread through infected downloads, email attachments, or compromised websites. Employing strong antivirus software and keeping systems updated can help reduce the risk of malware infections.
With the aid of Best Software Training Institute programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.
4. Insider Threats
Insider threats originate from individuals within an organization who may intentionally or unintentionally compromise security. These can include employees leaking sensitive information or neglecting security protocols. To combat insider threats, organizations should implement strict access controls and conduct regular training to foster a culture of cybersecurity awareness.
5. Distributed Denial of Service (DDoS) Attacks
DDoS attacks overwhelm a target’s systems with excessive traffic, rendering services unavailable to legitimate users. These attacks can disrupt business operations and lead to significant downtime. Organizations can protect themselves by investing in robust infrastructure and employing DDoS mitigation services.
Conclusion
The landscape of cybersecurity risks is continually evolving, presenting new challenges for individuals and organizations. By understanding the various types of risks and implementing proactive security measures, we can better protect ourselves and our data. Regular training, vigilance, and a strong security posture are essential in navigating the complexities of cybersecurity. Staying informed about emerging threats is key to maintaining a resilient defense in today's digital world.
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Spellen
- Gardening
- Health
- Home
- Literature
- Music
- Networking
- Other
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness



